- Private keys are the sole proof of ownership in crypto; losing or leaking them results in irreversible asset loss.
- Effective key management involves blending hot wallets for small sums, cold storage for significant holdings, and redundancy in backups.
- Multi-signature wallets require multiple approvals, thereby reducing the risk of theft, insider fraud, and single-point failure, while enabling shared governance.
- Best practices combine multi-signature with layered custody, backups, and institutional solutions, such as HSMs, MPC, and regulated custodians.
The Fragile Nature of Digital Ownership
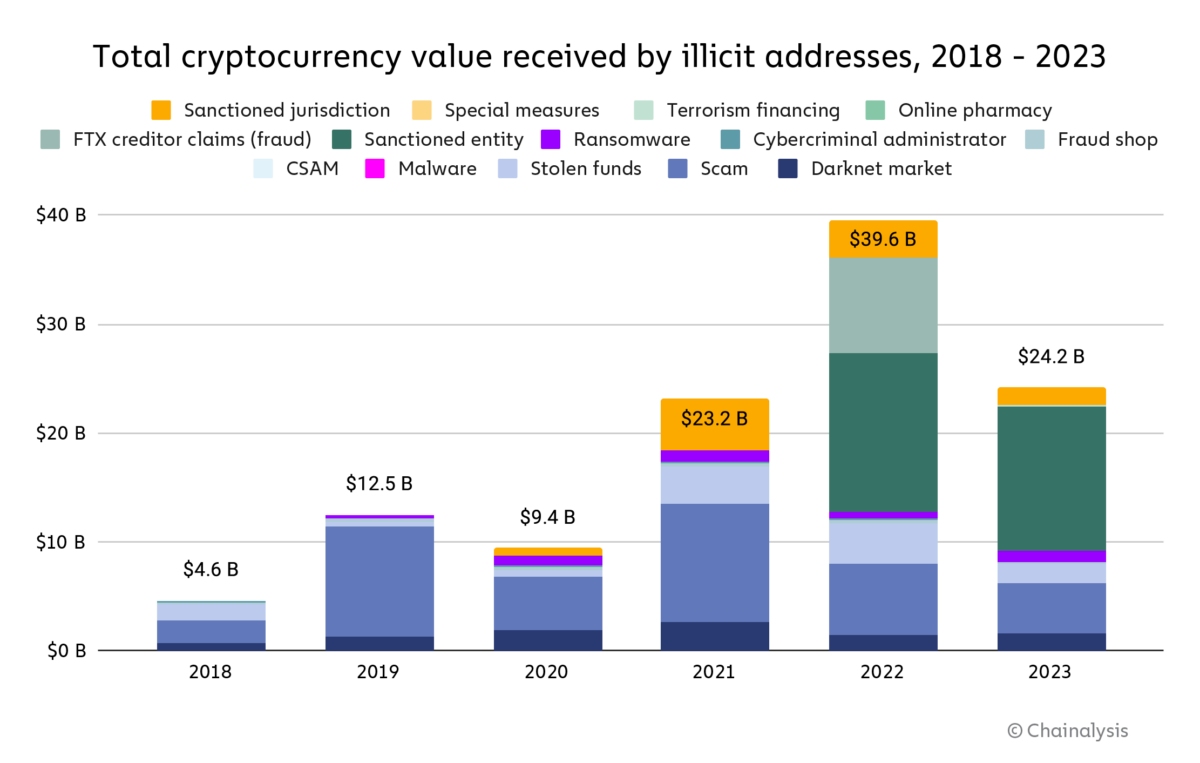
TradingKey - In the crypto world, permission is paramount. Unlike mainstream finance, where banks or custodians hold assets safely, digital ownership hangs on a single line of code: the private key. Whoever holds the key holds the funds. Self-sovereignty remains freeing yet risky. Billions have vanished into hacks, phishing, and simple mistakes as a result of investors underestimating the importance of key management.
Source: https://www.chainalysis.com
For institutions, traders, and longer-term investors, learning private key management is a necessity of survival. With the increasing maturity of the ecosystem comes the introduction of tools such as multi-signature wallets, which serve as insurance mechanisms designed to mitigate the risks of theft, fraud, or human error. Combining secure key storage and multi-sig configurations creates the foundation of secure crypto custody.
Why Private Keys Matter
A private key is the proof of ownership in cryptography. It authorizes transactions and allows you to send coins. Without it, you cannot access your assets, even you. Losing a key means losing your coins. Give it away, and a third party takes complete control immediately. There's no password reset recourse as you have with a bank.
This eventually puts private key protection at the forefront of best practices for digital assets. The number of high-profile thefts, whether from stolen exchanges, lost hardware wallets, or seeded leaks, is sufficient to illustrate the impermanence of this first line of defense. For private investors, the issue becomes a personal responsibility. For institutions, a systems one.
Source: https://www.chainalysis.com
The Basics of Key Management
There are several methods for storing private keys, each with its own set of trade-offs. Hot wallets, online through the internet, are convenient but susceptible to hacks. Cold wallets stored offline, either in software or on paper, limit the attack surface but require high handling. Custodian services relieve individuals of their responsibility but bring back third-party dependency.
It often makes the most sense to use a mix: small, expendable amounts stored in hot wallets for frequent use, and significant holdings stored in cold wallets. Redundancy counts as well; multiple secure copies of seed phrases spread out across various locations limit the chances of a single-point failure.
For institutions, professional-level custody solutions may integrate hardware security modules (HSMs), multi-layer access controls, and insurance-backed coverage. These are indicative of an increasing acceptance that key management needs to transition from an individual practice alert into an industry-wide best practice.
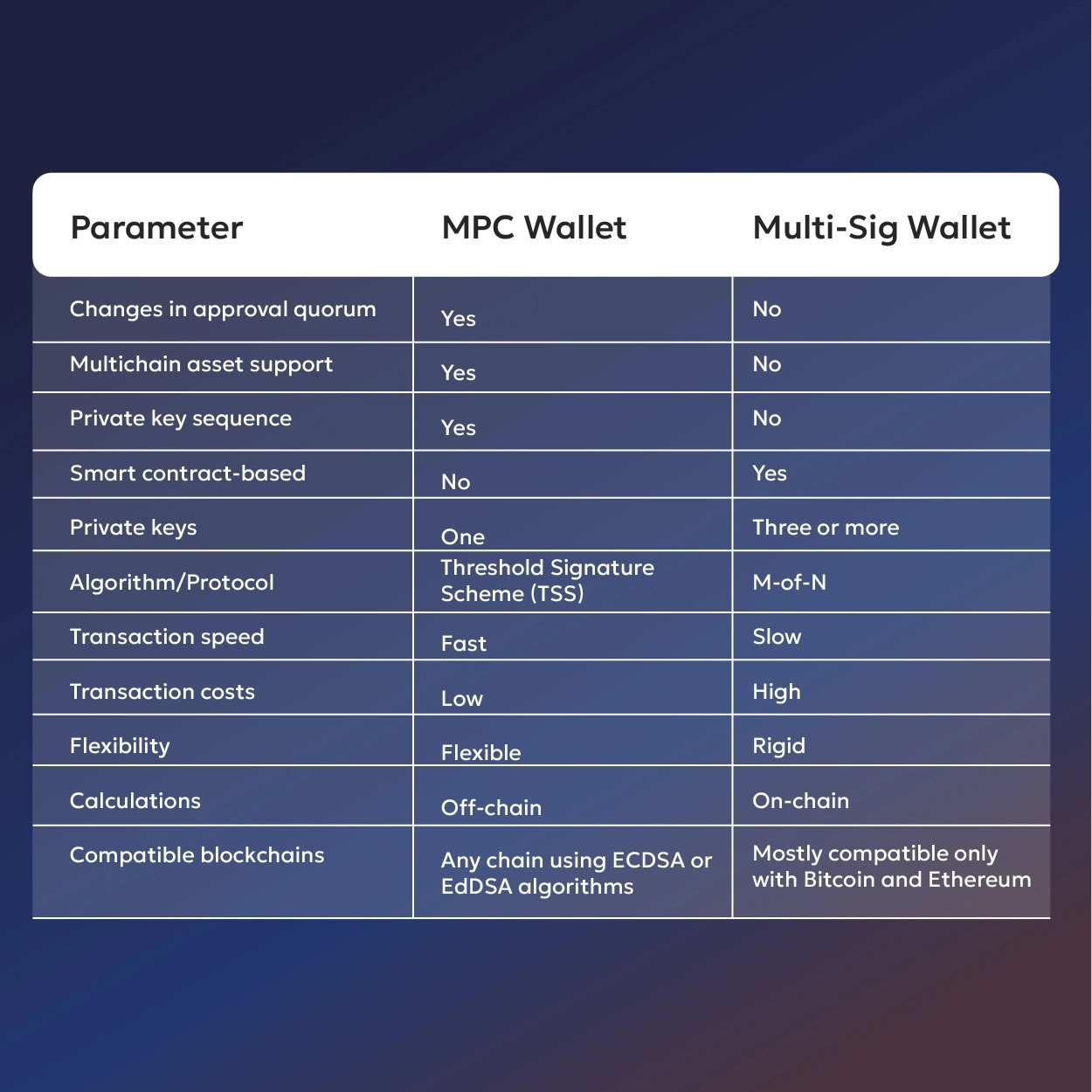
Multi-Signature
Multi-signature (multi-sig) wallets are a staunch innovation in custody. Rather than using a single key, they employ multiple keys to authorize transactions. A humble example of a 2-of-3 system could demand any two of three pre-nominated keys to sign before funds are transferred.
With this architecture, several risks are also eliminated. It guards against one stolen or phished key or one insider counterfeit. It also incorporates governance, with no single party exercising unilateral control over assets. It has built-in recovery mechanisms, such as one dead key being replaceable with the other two still being good.
Multi-sig finds exceptional value among businesses, funds, and DAOs where group control matters. Yet, solo individuals also benefit from distributing keys among trusted parties or devices.
Source: https://www.liminalcustody.com
Integrating Best Practices with Multi-Sig
Although multi-sig enhances security, it has no magic powers. Improper implementation, insufficient backup maneuvers, or overly complex configurations can introduce new threats. Optimized systems utilize multi-signature (multi-sig) alongside stringent key management practices.
These may involve segregating keys across various physical and digital realms. For example, a key on a hardware wallet, a second with a custodian stored securely, and a third in a physically distant safe deposit box. Access protocols should strike a balance between security and usability; if a system becomes too complicated, customers may cheat or use a workaround, resulting in a deleterious impact on safety.
These institutions also implement additional controls, such as time delays, as well as whitelisting of IP addresses and real-time checking of attempted transactions. These lower the likelihood of both internal robbery and external breach.
The Emergence of Higher-end Custody Offerings
With the natural evolution of the digital asset marketplace, custody has become an industry unto itself. There are now specialist companies providing multi-signature capabilities, institutional-grade vaults, and regulated custody under the supervision of financial regulators. These are often a mix of technology and governance, yielding good investment comfort.
Innovations such as multi-party computation (MPC) are also materializing. MPC eliminates the requirement for private keys to reside in a single location, with computation divided among multiple parties. Even further minimizing the risk of theft or loss. Although still nascent, MPC could be the next generation of custody's future, offering both security and usability.
Risks and Challenges
Even the best systems cannot eliminate risk. Human error is always a risk; lost seed phrase, misconfigured multi-sig, or forgotten recovery steps can. Freeze funds forever. Social engineering attacks can deceive even vigilant users into authorizing malicious transactions.
Legal and estate planning add further complications. Without adequate paperwork and access planning, digital assets may be missing at an owner’s passing. Families and companies are being forced to consider succession planning proactively, as traditional banking practices often no longer require it.
Cost and complexity may also deter adoption. Few investors are willing to buy institutional-grade custody or administer multi-sig procedures. For small portfolios, simplicity and safety are equally tightropes to walk.
Portfolio Considerations
For investors, the lesson is straightforward: asset protection is an integral part of the asset management process. A 20% return on crypto markets doesn’t matter if sloppy key management equals complete loss. Investing resources, time, dollars, and forethought in making custody a safe and secure practice isn't a choice; it's a base.
For individuals, this could be a hybrid model with cold storage, back-ups, and a minimal multi-sig configuration. For institutions, professional-grade custody, tiered governance, and insurance are essential. Either one has the same principle at play: redundancy, resilience, and self-control.
Just as investors diversify their portfolios to mitigate market risk, they must also diversify their custody strategies to reduce operational risk.
Conclusion: Security as Strategy
Private key administration and multi-signature configurations are no mere technical footnotes; they are at the heart of digital investing’s future, with a system developed around decentralization, shifting individual and institutional responsibility away from the bank. Those who gain mastery of custody will be well-positioned to reap the benefits of digital assets while avoiding potential disaster.
Those who overlook it risk joining the list of failed wallets or depleted accounts. When fortunes are measured in lines of code, control is tactical. Keep your keys safe, implement multi-signature, and understand that it’s the investment that serves as the safety measure in crypto.


