● Rapid digital-asset growth attracts evolving scams that cost billions, demanding skepticism and pattern awareness.
● Phishing remains the top entry point—verify URLs, avoid strange links, and never share seed phrases or private keys.
● Major frauds include Ponzi schemes, pump-and-dump scams, fake wallets/exchanges/apps, social engineering impersonations, and DeFi rug pulls/exploits.
● Protect by slowing down, using 2FA/cold storage, verifying teams/audits/contract addresses, leaning on trusted communities, and staying vigilant against AI-driven deepfakes.
The Dark Side of Digital Wealth
With the growth of digital assets has come unprecedented opportunities for investors. However, innovation is often found in exploitation. Thieves and scammers love high-updating-speed industries where hype frequently gets ahead of rules. Crypto, NFTs, and online trading forums are hotbeds of deception, serving as hunting grounds where billions are lost every year due to scams and phishing.
The problem isn’t that there’s fraud out there; there are the patterns. Methods evolve as investors become wiser. Others become recycled with new coats as investors become smarter. New technologies bring attackers new opportunities. For investors, learning about patterns isn’t paranoia, but knowing how to protect oneself. Survival is about seeing patterns, remaining disciplined, and never forgetting that when it comes to finances, if it seems too good to be true, it likely is.
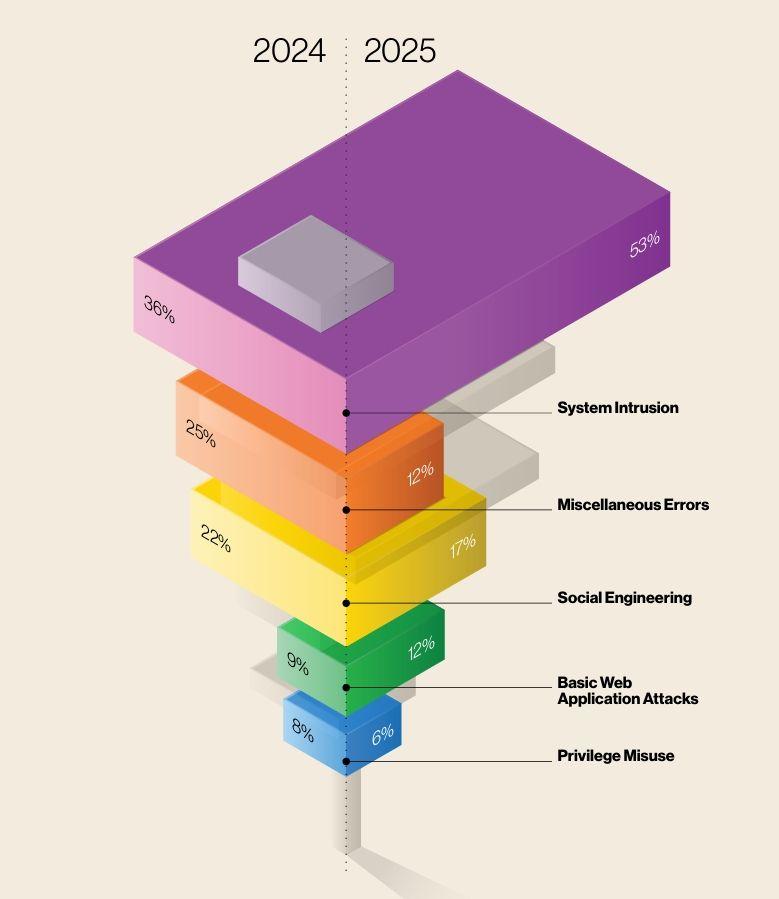
Source: https://www.keepnetlabs.com
Phishing as the Initial Strike Protection
Phishing is still the leading type of fraud in the digital assets sphere. Threat actors impersonate trusted websites, wallet vendors, exchanges, or social network acquaintances, even as they attempt to induce victims into handing out private keys or login credentials. Desperately compelling emails, bogus customer support interfaces, or spoof websites are all time-tested gambits.
Even more sophisticated is spear-phishing, where hackers tailor messages with information scraped from publicly available profiles or from chat rooms. Acting familiar makes it more likely you will succeed. Always the aim: get you to click, type, or sign something that relinquishes your control.
Protection is awareness. Always check URLs, never click on strange links, and remember that legitimate sites will never request your seed phrase or privacy key.
Investment Frauds: From Ponzi through Pump-and-Dump
Another large group of fraud is false investments. Ponzi schemes offer stable, unusually high returns with minimal risk, paying off old investors with new contributions until the system breaks. Pump-and-dump gangs inflate the values of esoteric tokens or NFTs before insiders sell their stock to unsuspecting latecomers.
These plans feed off greed and urgency. Social media influencers, Telegram channels, or shiny websites bring legitimacy. However, the mechanics are hardly altered; returns are not feasible, there's a lack of transparency, and exits are predetermined.
Knowing the red flags matters a lot: promised returns are certain, there is no proof of audits, and the teams are faceless. Real investment involves risks and disclosures, which scams can disguise.
Fool's Wallets, Exchanges, and Apps
Scammers also make fake wallets, exchanges, or phone apps nowadays. These look real at times and become top-listed on app stores, yet their purpose is almost instant theft once the funds are deposited. Spoof links to fake decentralized exchanges are spread during token airdrops, as tokens are abused through hype and the fear of missing out.
These are sophisticated scams sophisticated enough to deceive experienced investors. Defensive practices count: only download apps from legitimate sites, bookmark reputable sites, and double-check the wise and prudent contract addresses before using. With crypto, one wrong step can lead to permanent loss.
Social Engineering and Impersonation
Not all scams are technical. Most are dependent upon the psychology of man. In impersonation scams, scammers impersonate famous personalities, entrepreneurs, analysts, or even stars, to demand their victims' money or advertise mug shots. “Send one coin, get two back” scams have swindled millions of dollars by exploiting greed and faith.
Even more nefarious are romance and friendship scams, where attackers establish rapport for weeks before presenting phony investment opportunities. Victims are led to believe they are assisting a trusted associate while often realizing much too late that they've been conned.
Timeless lesson: check first before you trust, and never wire funds from a distance solely based on online relationships.
Rug Pulls and DeFi Exploits
Rug pulls occur when project developers execute an exit scam by divesting liquidity pools while leaving investors with worthless tokens. Others are outright exit scams; others employ sophisticated smart contracts that insiders can use undetected to withdraw funds.
Vulnerabilities of the smart contract also appeal to hackers. Codeworms may exploit code bugs and leech funds from well-meaning projects. These occurrences promote the aspect of due diligence, beyond teams, on technical audits.
Investors should distinguish between innovation risk and outright chicanery. Lack of clarity, phantom teams, or unaudited contracts are red flags.
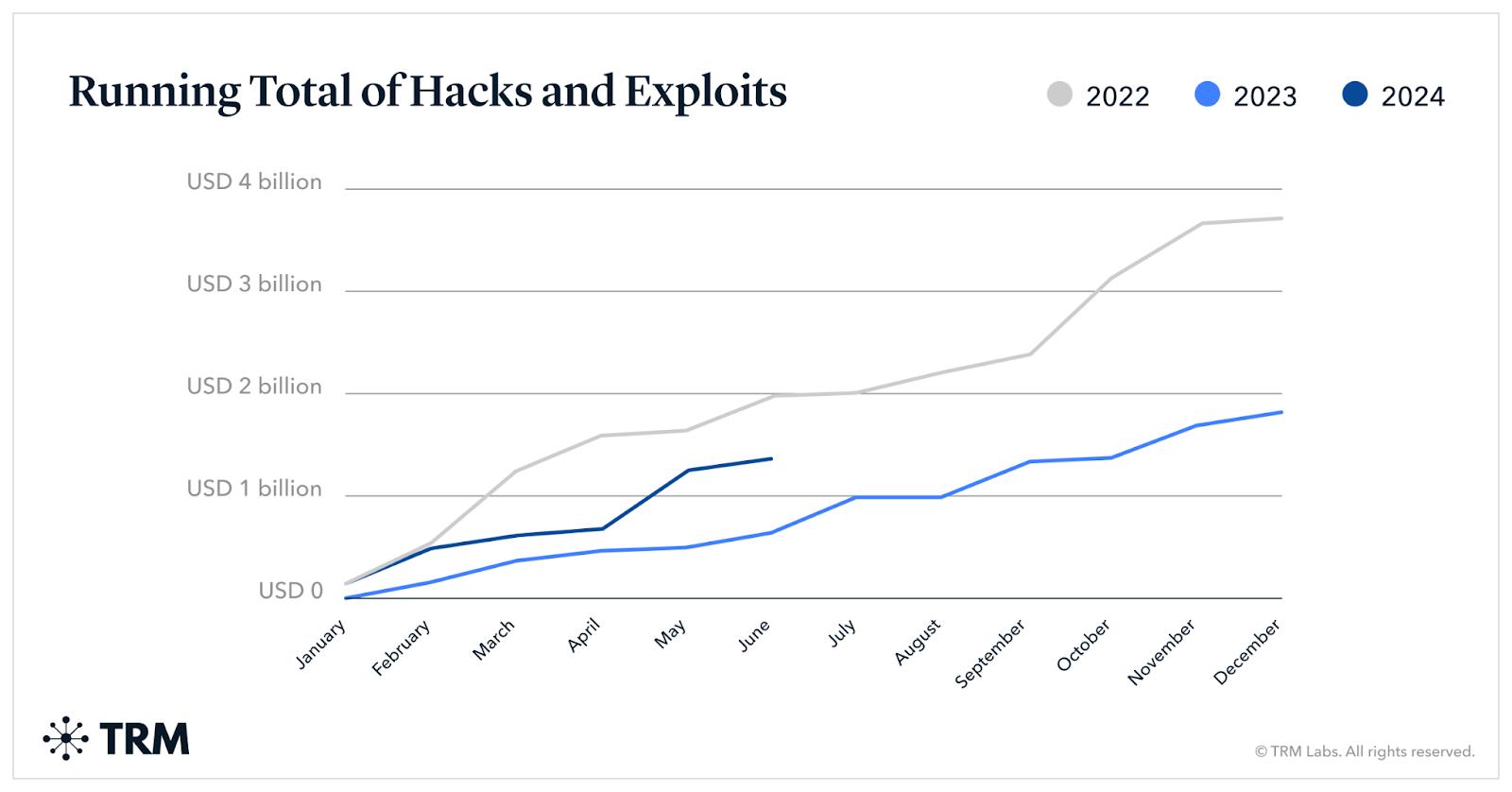
Source: https://www.trmlabs.com
Defence Plans
To avoid how-to-scam-you types, you require instituted processes and rigid disciplines. Firstly, secure first: do not trade private keys for martinis, keep the backups safe, and activate two-factor authentication. Secondly, and more importantly, act slow. Scams largely depend on urgency, an expire-period deal, phishing alert, or touted token sale. Act slow, check out later. It may cost you money but also earns you fortunes.
Third, bank on communities. Discussion boards, quality analyst sources, and reliable networks often spot sliders before the rest of the crowd. In doubt? Question. Scammers triumph through loneliness, where the victim has to act alone.
And finally, bear responsibility. Decentralized finance’s it’s “not your keys, not your coins”; the same principle can be applied to prudence too: not your prudence, not your safeguard.
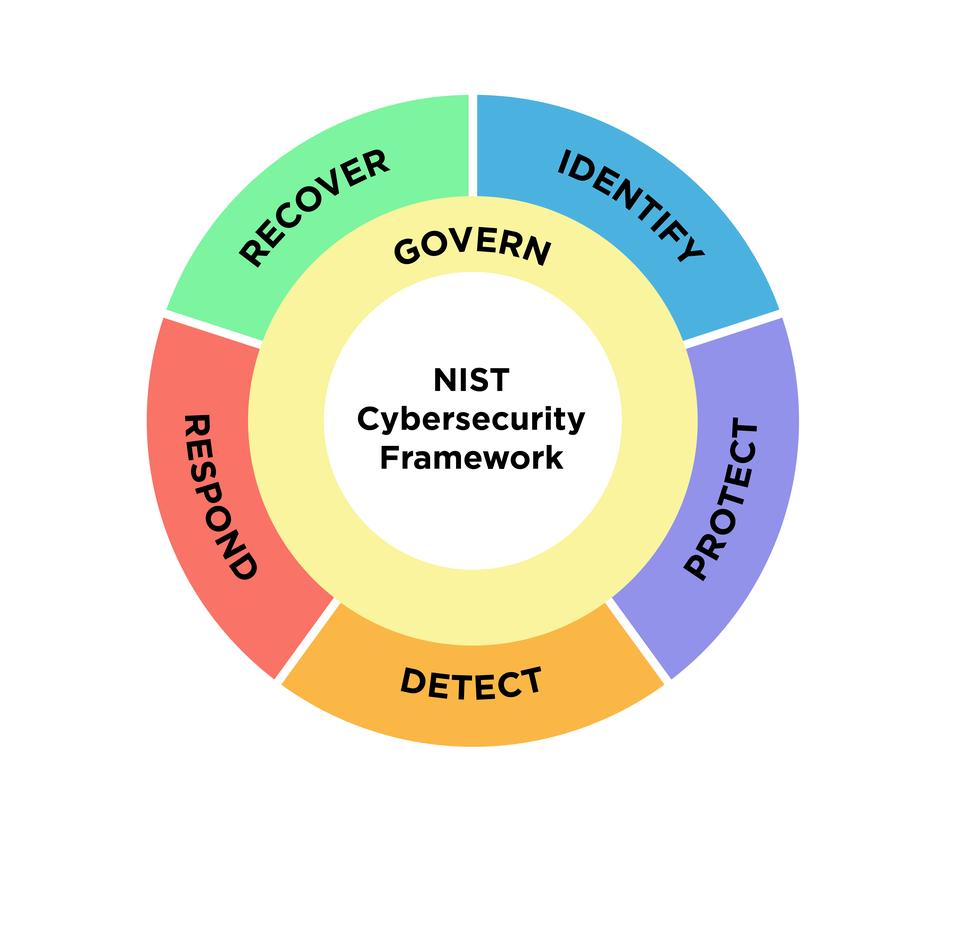
Source: https://www.nist.gov
Risks For What's Ahead
As technology advances, so too will scams. Deepfakes already enable large-scale impersonation. AI content could create convincing-looking but false customer support or marketing campaigns. Even old-saw investors could get mixed up about the difference between the truth and the lie.
Regulation will help but not deter risk. Frauds are never ahead by only half a step. In the end, investor education is the best defense. Those who remain educated, skeptical, and disciplined will move safely through the minefield.
Conclusion: Vigilance as Investment Strategy
Policy Scams and phishing are not footnote of the online era but the very heart of the risk. Investors who overlook phantom income as well as outright thievery will someday lose capital. But those who spot patterns, set defensive disciplines in place, as well as avoid being rush-bucketed will both hold capital as well as credibility.
Paranoia isn't the objective; prudence is. In the age of volatility and of innovation, the scoundrel will forever be the nagging threat. Inscribe prudence as part of your investiture process, however, and you turn an otherwise deadly peril into an acceptable risk. Because where the digital age of finance takes you is not where it lets you invest; it’s where it shields you.


